5 FREE Tips to Protect You from Hackers
Geopolitical hacking threats are increasing and you should be protected – Here are 5 free tips to keep your information safe As many of you know, with the current tension evolving between the United States and Iran, geopolitical hacking is becoming a real threat. On January 4th, 2020 an Iranian hacking group targeted a government…
Read MoreAre You Safe From Ransomware?
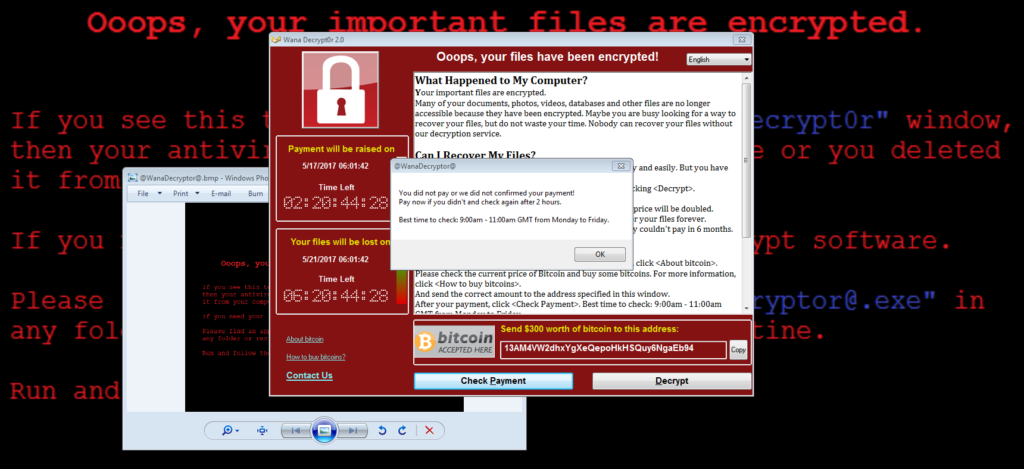
Are you protected from the threats of ransomware and malware? You may ask, what exactly is ransomware? Well, in a nutshell – Ransomware is a form of malware that is quickly evolving and becoming more and more common. Ransomware will unknowingly infect a computer and restrict users’ access until a fee (or ransom) is paid,…
Read MoreThe Importance of End-User Training
End-User Training Training is Just as Important as Cybersecurity. At TRACKtown, we cannot express the absolute importance of end-user training. An estimated 90% of all security breaches are attributed to user error – not software. There are many reasons an end-user can fail to truly understand cybersecurity protocol and how to use certain software, but…
Read MoreIs Your Encrypted Information Truly Safe From Attacks?
Your VPN provider may not be as secure as they claim. One way attackers can easily infiltrate, an unsecure VPN is to compromise employee’s credentials where there is not multi-factor authentication technology in place. Once information is accessed, your organization falls into the risk of a data breach – If your business is in the healthcare, legal, or any other field where compliance is a priority, you could risk huge fines and a significant loss of reputation. Without proper encryption, your private data may be collected and sold.
Read MoreStay Ahead of Hackers by Changing Your Passwords
What’s the best way to change your passwords? Often, and with best practices in mind. How frequently do you change your passwords? An alert pops up on your computer: It’s time to change your password again. Sigh. Fine. You’ll just change from password4! to password5! and— Not so fast. Regular password changes are meant to…
Read MoreDemonstrating Compliance with Data Security Regulations Can Be Easy if You’re Prepared
To help demonstrate you’re compliant with access control requirements, you should have clear policies and procedures about who gets access to what, what kind of passwords are required, and how often those passwords are updated. If you don’t have a way of automatically tracking and logging password use, it’s very hard to enforce those kinds of policies — or to show you’ve followed them after an incident.
Read MoreWho Has Access to Your Systems?
employee left your business, did you revoke their access to your IT systems?
Are you sure? Do you have a way to check?
What kind of
information could your former employees get if they still hold valid
credentials (even though they no longer work there)? Depending on your
business, the answer could include client data, proprietary research, or your
financial information.
Strong Security Starts with Strong Passwords
We have been thinking a lot about client security lately. It’s all too easy to think passwords are a nuisance—when really they’re essential to keeping your data and your business safe If you use the same password for multiple systems—online shopping, email, your company’s cloud bookkeeping solution, etc.—you’re not alone. Even Facebook founder Mark Zuckerburg…
Read More